Three people have been indicted on charges of masterminding a $400 million hack reportedly linked to failed cryptocurrency exchange FTX. The grand jury indicted them as follows: Arstechnica The nearly two-year SIM swapping spree resulted in two reported counts of conspiracy to commit wire fraud and aggravated identity theft and access device fraud.
According to prosecutors, Americans Robert Powell, Carter Rohn, and Emily Hernández carried out the SIM swap attacks between March 2021 and April 2023.
However, court documents cited by ArsTechnica do not mention FTX or its founder Sam Bankman-Fried by name. Instead, it was given the name Victim Company-1. subsequent bloomberg Today’s report cites anonymous sources confirming that Victim Company-1 is in fact FTX.
“On or about November 11, 2022, Hernandez used a fake ID containing details of an FTX employee to convince AT&T to transfer his mobile phone account to a different SIM card.” bloomberg said. “Powell, the alleged ringleader of the group who goes by the online nicknames ‘R$’ and ElSwapo1, used various authentication codes to access FTX’s cryptocurrency wallet.”
The indictment lists several targets, but one section in particular has led to much speculation that the hack may have targeted FTX on the day the company filed for Chapter 11 bankruptcy in late 2022.
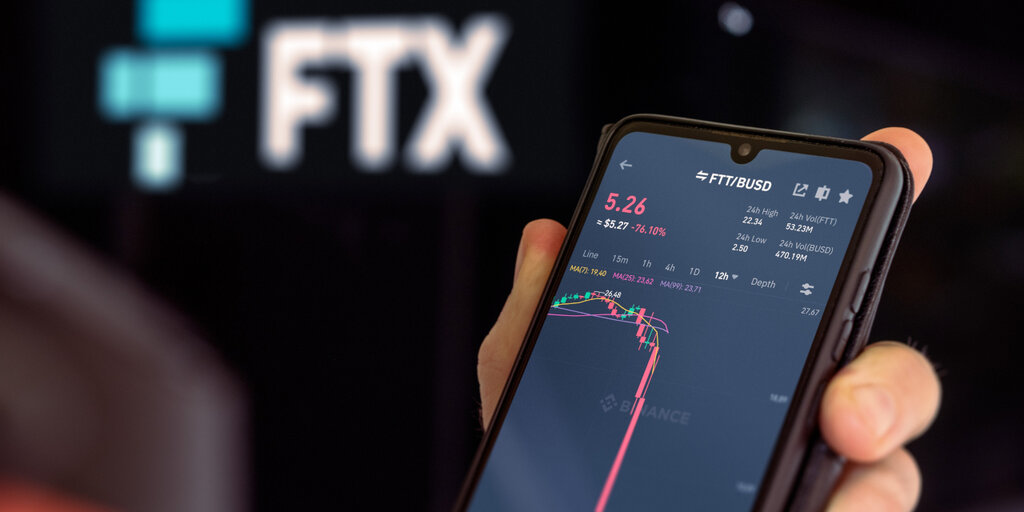
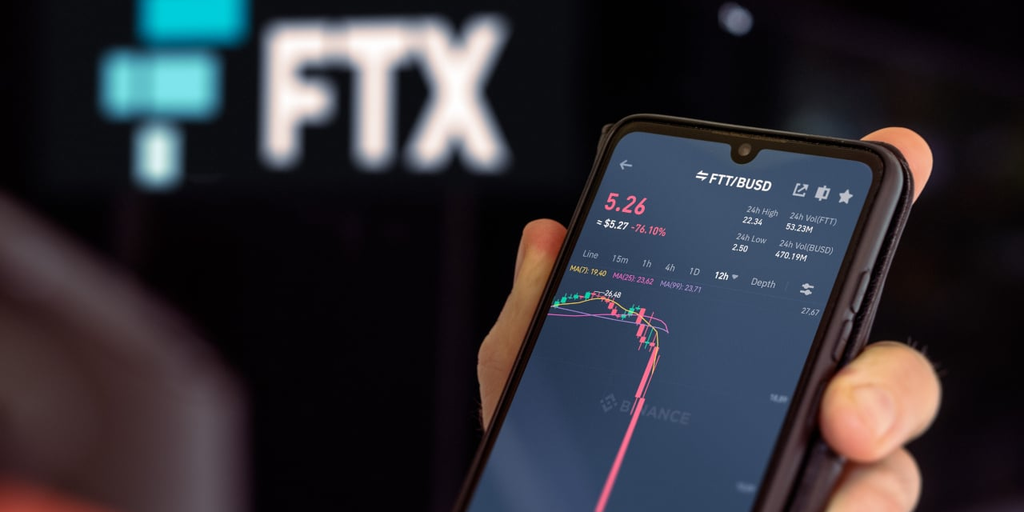
The prosecution said, “Continuing from around November 11, 2022, to November 12, 2022, the conspirators transferred over $400 million worth of virtual currency from the virtual currency wallet of Victim 1 to the virtual currency wallet managed by the conspirators.”
“We are investigating anomalies in wallet movements related to the consolidation of FTX balances across exchanges,” FTX US General Counsel Ryne Miller said in a then-deleted tweet.
According to blockchain detective ZachXBT, more than $650 million was stolen in 24 hours.
SIM jacking, or SIM swapping, is a type of cyberattack that steals someone’s phone number by instructing a mobile carrier’s customer support representative to transfer the number to another SIM card. Hackers can then use the reassigned SIM to bypass two-step authentication and gain access to the victim’s online accounts, such as bank accounts, social media accounts, and email accounts.
Edited by Ryan Ozawa.