LockBit, described by law enforcement as “one of the world’s most prolific ransomware gangs,” has been dismantled through a coordinated campaign involving officials from the United States, the United Kingdom and six other countries, multiple agencies announced today.
The U.S. Department of Justice has unsealed an indictment against two Russians, Artur Sungatov and Ivan Kondratyev, for allegedly carrying out LockBit attacks against U.S. companies. Sungatov has reportedly targeted manufacturers, insurance companies and other companies in at least six states since January 2021.
“Today, American and British law enforcement agencies are taking away the keys to criminal activity,” U.S. Attorney General Merrick Garland said in a release from the Department of Justice (DOJ). “And we went one step further and obtained keys from the seized LockBit infrastructure to enable victims to decrypt captured systems and regain access to their data.”
Kondratyev, known online as “Basterlord,” has reportedly distributed ransomware to a variety of targets since August 2021, from city governments to companies in Oregon, Puerto Rico and overseas.
The Treasury Department’s Office of Foreign Assets Control (OFAC) sanctioned Sungatov and Kondratiev, barring them from doing business with U.S. individuals and entities, freezing all assets under U.S. jurisdiction, and removing nine Bitcoin and Ethereum wallet addresses linked to them. 1 added to sanctions list. .
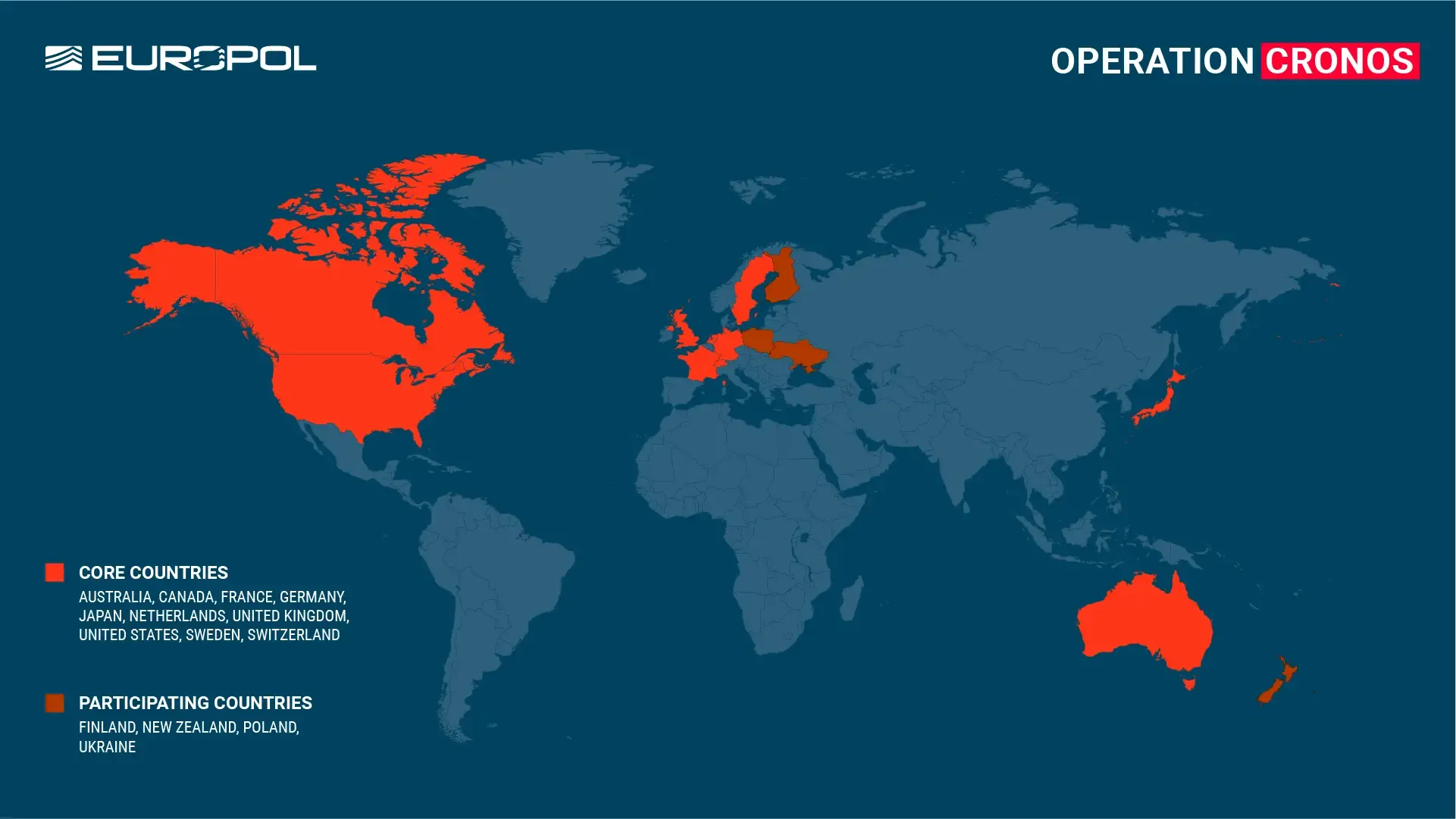
The months-long “Operation Kronos” resulted in the seizure of dozens of servers across Europe, North America and Australia used to carry out LockBit’s ransomware attacks that encrypt victims’ data and extort them for payment, according to an announcement Tuesday. At Europol.
Authorities also took control of a portal on the dark web where LockBit posted sensitive data stolen from victims who refused to pay.
“We have now destroyed the online backbone of the LockBit group, one of the world’s most prolific ransomware organizations,” Europol Executive Director Catherine De Bolle said in a statement.
“The first step to putting cybercriminals behind bars is to report cybercrime when it occurs,” she added. “The sooner people report, the sooner law enforcement can evaluate new methodologies and limit the damage they can cause.”
What was LockBit?
LockBit first appeared in early 2020 and used ransomware that encrypted victims’ files and locked them on the network unless a ransom was paid, usually in cryptocurrency. Payments were typically requested in Bitcoin, according to the DOJ’s indictment.
Like other “ransomware-as-a-service” organizations, LockBit operates through a core group of developers who create malware tools and run the infrastructure, then recruit affiliates to infect targets in return for a cut of the proceeds. LockBit’s developers have maintained a dashboard where affiliates can launch attacks with just a few clicks.
According to Europol, LockBit surpassed other ransomware variants in 2022 to become the most widely distributed ransomware worldwide. According to the Justice Department, the syndicate sought more than $120 million in ransom from more than 2,000 victims worldwide, with total demands expected to reach hundreds of millions of dollars.
LockBit gained notoriety for its use of “triple extortion,” threatening victims not only with encrypted data, but also with stolen information exposure and lethal denial-of-service attacks.
The authorities counterattacked
The “Operation Kronos” task force, comprised of law enforcement agencies from 10 countries, had been attacking LockBit for months. The turning point came when LockBit seized dozens of command and control servers it relied on to distribute ransomware and manage its operations. According to Europol, authorities now have “controlled the technical infrastructure that allows all elements of the LockBit service to operate.”
As a result, “more than 14,000 malicious accounts responsible for breaches or infrastructure were identified and requested for removal,” the agency said.
Additionally, French and U.S. officials have arrested or prosecuted a growing number of LockBit members. Poland detained ransomware suspect Ivan Kondratiev in October 2022, and another Russian national was arrested in Ukraine.
Three international arrest warrants have been issued in connection with the recent attacks. French authorities also secured five indictments. Meanwhile, authorities froze cryptocurrency wallets that LockBit members reportedly used to pay the ransom.
“This underscores our commitment to disrupting the economic incentives that drive ransomware attacks,” the Justice Department said.
Helping victims recover
By taking control of the LockBit system, authorities obtained decryption keys that allowed hundreds of victims to regain access to their data.
“We are changing the game for LockBit by providing decryption keys, unlocking victim data, and tracking LockBit criminal affiliates around the world,” Deputy Attorney General Lisa Monaco said in the release.
Victims of LockBit attacks are encouraged to contact law enforcement through the Department of Justice website to see if they can decrypt their files.
These solutions are also available for free on the ‘No More Ransom’ portal, available in 37 languages. To date, more than 6 million victims worldwide have benefited from No More Ransom. No More Ransom includes over 120 solutions to decrypt over 150 types of ransomware.
Monaco said the operation was a major blow to one of the most aggressive ransomware groups, but would not be the final act against cybercriminals.
“Our investigation will continue and we are determined to identify and prosecute all members of LockBit, from developers and managers to affiliates,” said U.S. Attorney Philip Sellinger. “We will highlight them as wanted criminals. They will no longer hide in the shadows.”
Editor: Andrew Hayward