
The hackers claim to have accessed law enforcement systems used by clients including cryptocurrency exchanges Coinbase and Binance.
But none of the parties involved – the security firm that reported it, the company believed to have been affected, or the cryptocurrency exchange at risk – seems to agree on whether to take the hacker’s threat seriously.
Hudson Rock, a cybercrime intelligence company, released the following claims: InfoStealers The blog claimed that a threat actor going by the name “Tamagami” gained access to law enforcement systems, including Kodex. This is the system used to process subpoena requests from companies including Chainlink, Coinbase, and Binance.
The hacker offered to sell access to the account for $5,000 and request individual subpoenas for $300. If any of the hackers’ claims are valid, anyone who purchases fraudulently obtained credentials could use them to impersonate law enforcement and subpoena all sensitive data related to cryptocurrency exchange users.
said Alon Gal, CTO of Hudson Rock. decryption They claimed that while “it is difficult to verify Tamagami’s claims,” they accessed Google and Meta’s law enforcement systems and provided “what appear to be real images from the platforms.” He added that the user had around 250 reputation points on cybercrime forums. This “indicates that users vouch for their legitimacy.”
Hudson Rock also claimed to have identified more than 50 different sets of credentials for Google’s law enforcement systems from various Infostealer infections, and Gal said hackers claiming to sell access to law enforcement systems were not isolated incidents. They pointed out that it is a known threat vector.
“The reported illegal sale of access to the law enforcement request portal does not constitute a violation of Binance’s systems,” a Binance spokesperson said. Decrypt. “Instead, law enforcement accounts may be compromised.”
They added, “Through thoroughly documented processes and ongoing monitoring of compromised accounts, we are committed to protecting user data from all forms of unauthorized access.”
A Kodex spokesperson disputed the claim in an emailed statement. decryption“People are confusing access to the Kodex platform with access to features.” Screenshots advertised on hacker forums and Telegram channels “show only an incomplete process. There is no evidence that a request was actually sent or that any data was sent.” It actually came back.”
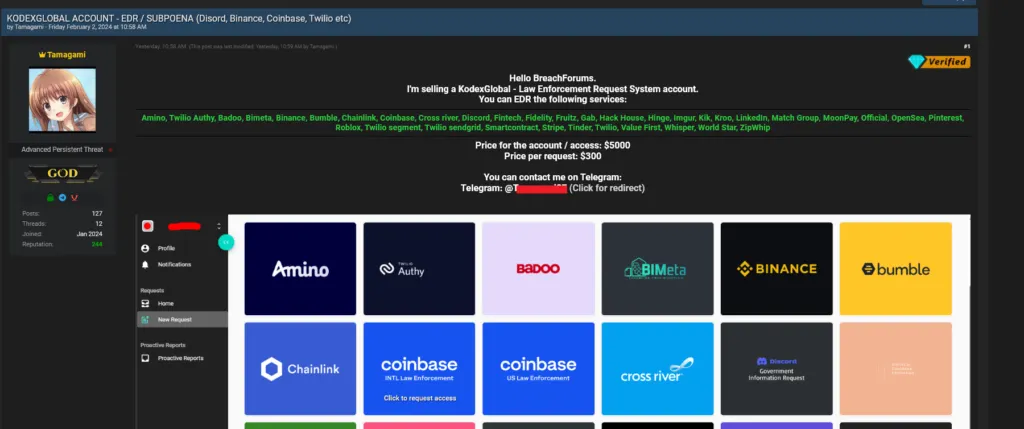
The company operates under the assumption that simply accessing law enforcement email addresses is not sufficient verification, the spokesperson said, adding that it monitors account activity for suspicious activity.
“Several flags were tripped in our system to suspend the account before the request was sent,” a spokesperson said in an email, adding that all accounts associated with the flagged email domain will be suspended until re-verified by the Kodex team. . “Emergency data requests (EDRs) undergo additional verification steps and this account has not been approved,” they said.
Edited by Stacey Elliott.



