The Rise of DDoS Attack in Blockchain Network
Have you come across situations where websites become very slow to respond? On other days, you might have accessed the same websites without any issues. What could have led to the delay in loading the website or accessing its functionalities? The answer would point to DDoS attacks or Distributed Denial of Service attacks. Such types of attacks focus on exploiting the setbacks in the design of a website. The way in which blockchain DDoS attacks work shows that they can lead to slow performance of a website, and in some cases, it would not even load. Blockchain networks are inherently immune to the Distributed Denial of Service attacks.
DDoS attacks rely on flooding a website with an overwhelming amount of traffic that would ultimately lead to the website crashing. Blockchain is safe from traditional DDoS attacks because the decentralized design excludes the possibility of any single point of failure. However, you cannot ignore the possibility of a blockchain DDoS attack completely because of decentralization.
Hackers would not flood the network with transaction requests or pings. On the contrary, they might opt for flooding the blockchain with spam transactions. It would ultimately lead to congestion in the network that would slow down the completion of legitimate transactions. Let us learn more about DDoS attacks in blockchain and how you can resolve them.

Working of a DDoS Attack
The first thing you need to learn before exploring the impact of a DDoS attack in blockchain network is the basic definition of a DDoS attack. It refers to any type of attack that overloads the systems of a website with massive volume of internet traffic. DDoS attacks aim at bringing the website down and reducing its capacity for functioning properly.
Hackers can deploy a DDoS attack through exploitation of bottlenecks in the design of the website. The process generally involves thousands of bots that would connect to the website and use bandwidth. The bots would reduce the resources that are available to actual users, thereby preventing them from connecting to the website.
If you want to know how to identify DDoS attack, then you must know about the way in which it works. DDoS attacks happen primarily for two distinct reasons. First of all, hackers can hold the website hostage and demand that the website owner should pay to stop the attack. Generally, businesses have been forced to pay the ransom to attackers when they could not fix the vulnerability quickly.
On the other hand, DDoS attacks could also serve as an attempt to affect the reputation of a company. Malicious competitors can deploy a DDoS attack to showcase that the company does not have the resources to counter a DDoS attack. With almost 20,000 to 30,000 DDoS attacks happening every day, it is important to find effective ways to resolve them.
Build your identity as a certified blockchain expert with 101 Blockchains’ Blockchain Certifications designed to provide enhanced career prospects.
Variants of DDoS Attacks
The next important thing you need to learn for exploring the impact of DDoS attacks in blockchain networks is the types of DDoS attacks. You can find different types of attacks, including layer 4 DDoS attacks that can target different bottlenecks in a website. Some of the common DDoS attacks include volumetric attacks, application attacks, protocol attacks, TCP connection attacks, and fragmentation attacks. Here is an overview of the impact of the different DDoS attacks on a website.
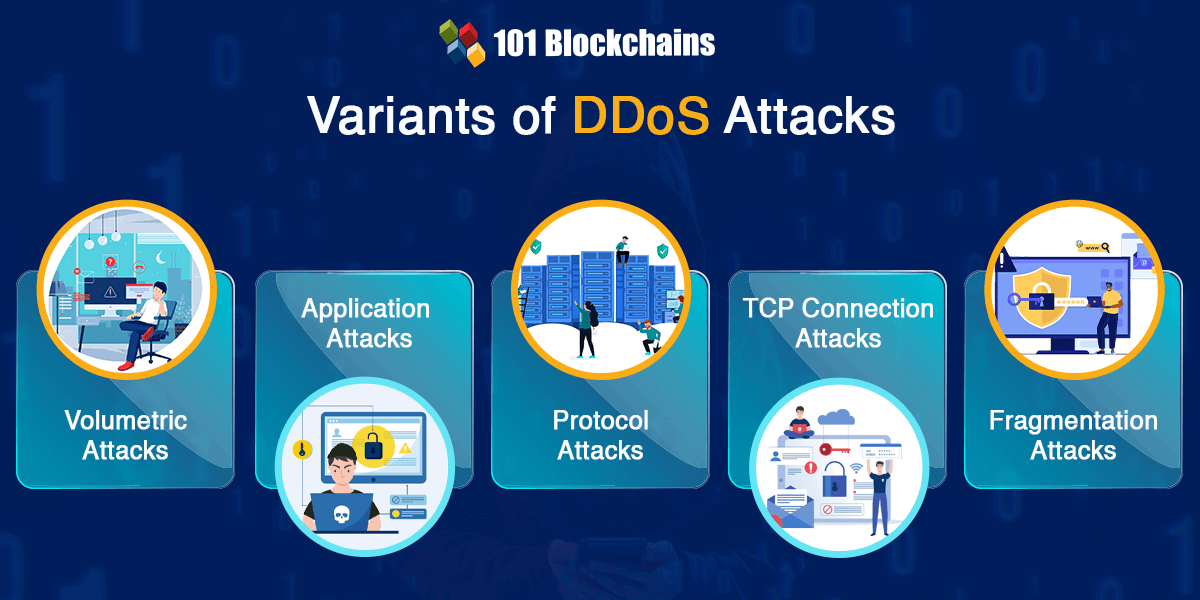
Volumetric attacks aim at consuming the bandwidth within the target network or service or between the target network or service and the rest of the internet. The primary objective of volumetric attacks revolves around ensuring congestion. Volumetric attacks consume bandwidth and lead to difficulties in connection between a website and the internet.
Application attacks are also another important variant of DDoS attacks. You can understand the impact of DDoS attack in blockchain network by identifying how application attacks target the application rather than the surrounding infrastructure. One of the most alarming aspects of application attacks is the fact that you would not need powerful systems. Hackers can deploy application layer attacks by using smaller systems with lower computing power.
Protocol attacks work by affecting the ability of the network to complete functions. For example, hackers could send incomplete data or packets of data. The incomplete packets could lead the server to wait to receive the remaining data or connection requests.
Another notable variant of DDoS attacks points at TCP connection attacks which focus on occupying connections. TCP connection attacks consume all the available connections to infrastructure devices, including application servers, load balancers, and firewalls. On top of it, devices that are capable of maintaining state across millions of connections could also be vulnerable to such attacks.
-
Fragmentation Attacks
Fragmentation attacks focus on using packets of data transmitted to websites. The website receives a sudden surge in fragmented data. The system must reassemble the fragments to process the data or request. However, sending more data in packets could hamper the ability of websites to assemble the data, thereby reducing the performance.
Start learning Blockchain with World’s first Blockchain Skill Paths with quality resources tailored by industry experts Now!
How Can You Identify DDoS Attacks?
The ideal approach for finding answers to “Why are DDoS attacks increasing in blockchain?” would also involve identifying DDoS attacks. One of the most common symptoms of a DDoS attack is the unavailability of a website or service. However, you can also find other symptoms, such as performance issues or legitimate spikes in website traffic. You can use penetration testing for a safe and comprehensive attack simulation that can expose complex vulnerabilities. Some of the popular penetration testing traffic analytics tools could help in spotting the signs of a DDoS attack.
DDoS attacks might be identified in the form of suspicious traffic coming from a single IP range or IP address. You can also find how to identify DDoS attack by checking for unexplained surges in requests to a single endpoint or page. DDoS attacks could also take the form of a surge in traffic from users who have a similar behavioral profile, such as web browser version, device type, or geolocation. Another notable sign of DDoS attacks is visible in odd traffic patterns, such as spikes in traffic at odd hours or infrequent spikes.
You should also notice that DDoS attacks also showcase different signs according to sophistication and length. DDoS attacks could be long-term attacks or burst attacks. With the rise of IoT technology and powerful computing devices, the resources for generating more volumetric traffic have been increasing. Therefore, attackers could create higher traffic volume in shorter durations. You can find that burst attacks are difficult to detect as they only last for a few seconds or a minute.

What is DDoS in Blockchain?
You can learn how blockchain DDoS attacks work by understanding how blockchain technology works. The most prominent highlight of blockchain networks is decentralization by design. Blockchain networks have a few or thousands of nodes working on verification of transactions. Users would submit transactions on the network, and all the nodes would work collectively to validate the transaction. The decentralized design ensures that a traditional DDoS attack would only achieve success in compromising one or few nodes. However, it would not affect the network as all the other nodes continue their operations.
With the decentralized design, blockchain networks are resistant to traditional DDoS attacks. However, it does not make them completely immune to DDoS attacks. Different types of blockchain networks have different levels of resistance towards DDoS attacks. You can find the cause of layer 4 DDoS attacks by exploring different factors.
The factors include the number of nodes responsible for validation of transactions in the blockchain network, node client diversity, total network hash rate, and confidentiality of validator schedule. For example, a blockchain network with few nodes that run the same client would be more vulnerable to DDoS attacks. On the contrary, a blockchain network with thousands of nodes and running different clients would be more resistant to DDoS attacks.
Get familiar with the terms related to blockchain with Blockchain Basics Flashcards.
How Do DDoS Attacks Manifest in Blockchain Networks?
DDoS attacks in blockchain networks emphasize compromises in the protocol layer rather than attacking the individual nodes. The two common ways to deploy a DDoS attack in blockchain network include smart contracts attacks and transaction flooding. Here is an overview of the two prominent ways in which you can find DDoS attacks in blockchain networks.
Transaction flooding is one of the most common variants of DDoS attacks in blockchain. Most of the blockchain networks have a fixed block size. Every block has a specific upper limit for the number of transactions it can manage. It is important to note that blocks in a blockchain network are produced at pre-defined intervals. The pending transactions that cannot find a place in the current block would go into the mempool of a blockchain. The transactions would remain in the mempool until they are verified and included in the next blocks.
Hackers can implement a blockchain DDoS attack through transaction flooding by spamming the network with incomplete transactions. As a result, it would prevent the confirmation of legitimate transactions, which would go into the mempool. The attack would help in slowing down the operations of the blockchain network and legitimate users would have to pay an extremely high fee for validating their transactions.
Hackers could also implement a DDoS attack through smart contract hacking. Such types of attacks would only affect blockchain networks that offer support for smart contracts. Different blockchain networks have different levels of resistance to such attacks. You can also find an explanation for questions like ‘Why are DDoS attacks increasing in blockchain?’ in the continuously growing usage of smart contracts. Hackers could carry out a DDoS attack by sending a transaction that requires consumption of more computing resources. As a result, the network could not add other legitimate transactions, thereby leading to results similar to transaction flooding.
Excited to learn about the critical vulnerabilities and security risks in smart contract development, Enroll now in the Smart Contracts Security Course
Effect of Blockchain DDoS attacks
The review of the two prominent ways in which hackers could implement DDoS attacks in blockchains shows that the attacks prevent the addition of new transactions. However, you can learn how to identify DDoS attack for blockchain networks by checking for other signs. Blockchain DDoS attacks could also lead to the following outcomes.
Blockchain networks follow a peer-to-peer model in which every node receives a block or transaction and sends a copy to all neighbors. All the nodes would receive different copies of same transaction. As the transaction flooding leads to more transaction volume, it would eat up the network bandwidth thereby leading to congestion.
The impact of a blockchain DDoS attack is also visible in how it leads to node failures. Nodes have to deal with an extremely high number of transactions, which would put pressure on the memory or CPU and could crash.
Want to explore an in-depth understanding of security threats in DeFi projects? Enroll now in the DeFi Security Fundamentals Course
How Can You Prevent Blockchain DDoS Attacks?
The best approach for ensuring security against blockchain DDoS attacks involves increasing the scale of decentralization. On the other hand, the process of achieving decentralization would take more time. Therefore, you should choose effective safeguards to avoid the blockchain network becoming a victim of DDoS attacks. It is important to ensure that all nodes on the network have adequate storage, network bandwidth, and processing power. You should also identify and exclude potential spam transactions from the blocks that are likely to consume more computation resources.
Start your journey to becoming an expert in Web3 security with the guidance of industry experts with Web3 Security Expert Career Path
Conclusion
The rising volume of DDoS attacks in blockchain has created a notable concern for businesses seeking blockchain as a tool for digital transformation. At the same time, it is important to note that it is impossible to achieve complete immunity against blockchain DDoS attacks. You can identify the solutions for DDoS attacks by learning how blockchain DDoS attacks work and the best practices for diagnosing the signs.
Malicious actors could implement DDoS attacks through transaction flooding and attacks on smart contracts. However, you can ensure safety against DDoS attacks in blockchain networks by building secure smart contracts. On top of it, you can also rely on optimization of the nodes with better network bandwidth, storage, and processing power for handling DDoS attacks. Learn more about web3 security and the solutions for blockchain DDoS attacks right now.

*Disclaimer: The article should not be taken as, and is not intended to provide any investment advice. Claims made in this article do not constitute investment advice and should not be taken as such. 101 Blockchains shall not be responsible for any loss sustained by any person who relies on this article. Do your own research!